Until recently, your smartphone has been a private place. Your apps, personal information, and contacts, were all safely stored within a locked screen. However, hackers never sleep. There is always someone, somewhere, hard at work on the next big breakthrough. And now hackers have it.
In order to avoid becoming a hacker's next victim, you've got to be informed of the latest system vulnerabilities and keep your software updated. There are also companies on your side, who constantly guard against the malicious intent of hackers. Stay updated by checking their social networks for news.
Here's a recap of recent events, including a look at how hackers gain access to your phone.
Headphone Hack
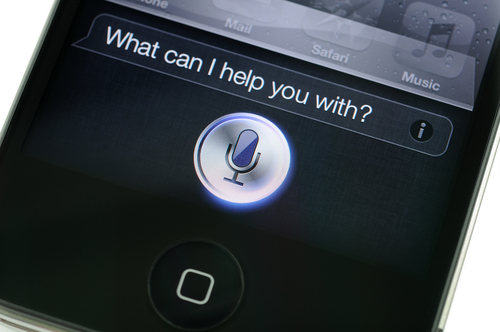
While this may be less of a hack and more of a malicious trick, you'll never keep your headphones in your phone again. A French government agency discovered they could control phones with silent (to the human ear) radio waves that your iPhone's Siri, or your Android's Google Now, would identify as voice commands.
If you leave headphones plugged into your phone, hackers can use those headphones as an antenna, which makes your phone more easily hacked. With this technique the hacker can make your phone download malware, send phishing scams through email, Facebook, Twitter, and other social network sites, or even have your phone call theirs, turning your phone into a listening device.
There are some limitations of this hack, ones which you can take advantage of for your protection. The plugged in headphones mentioned above, only work with this hack if they have a built-in microphone. And if your phone doesn't have Siri or Google Now enabled from your lock screen, the hacker can't access the program he needs. Most phones require the user to press a microphone button on the screen before they speak, which enables the voice command options.
Other Hacks to Watch For
MSpy is a surveillance app that tracks all received and dialed calls. It collects all texts, photos, and emails, and also monitors web history. The drawback of this app is that the person who uses it must have access to your phone. If you keep a healthy password on your lock screen, you should be in the clear.
Have you noticed all of the free charge stations in airports, malls, and other tech stores? Well, be careful where you plug in your phone. A USB charge station is a direct line of access. Some free charge stations have been outfitted with malware that is downloaded by your phone as soon as you plug in. Experts estimate that your phone is compromised within one minute if you use a malicious plug.
Beware of free Wi-Fi. Though coffee shops like Starbucks offer free Wi-Fi, tread carefully. A hacker can set up another Wi-Fi hotspot of their own and title it something similar, for instance, "Starbucks 2." Some people will probably connect, and as soon as they do their phones are open for attacks. The hacker can then load malware on their phones which attacks email and personal contacts, which in turn sends out phishing schemes for money and more personal information.